Note: This article was first published on www.procloudguru.com by Alpesh .Since the website is down, I am publishing the content here.
This article is about Azure AD integration with Qualys which is not formally documented with Qualys and is not listed as on Azure AD App gallery. That being said, not just Qualys but any SAML aware app can be integrated with Azure AD.
I am listing down a few benefits of doing this. Frankly, I don't see a downside to this in anyway because if you are already paying for the Azure AD premium licenses then this is the first thing you should be doing. Reason being Microsoft spends huge amount of money in ensuring the Azure/O365 infrastructure is secure and continues to invest in ensuring the security of the infra. As an organization you would want to leverage on their already available infra rather than spending valuable dollars on securing SAML which to you is not a primary business.
The entire process was very smooth and the Qualys support engineers we worked with were quite knowledgeable and knew what was required from them. I am not going to write about the steps taken by Qualys engineers as I am really not aware of what they did at their end. However, the entire process was very simple and took no more than an hour to set up the whole infra.
Before I go to the actual steps here are the benefits of above integration.
Some Challenges:
a) Qualys confirmed they are SP initiated. If we were to setup SP initiated infra, we have to either leverage on our existing setup for ADFS and ensure we have Reverse Proxy setup for the SP to reach our IDP. If existing infra is not available, then setup new infra. More Cost.
b) Because this is SP initiated sign on you need to ensure that you have a multi-factor auth protecting your ADFS infra. Even more cost.
c) Always concerned about DLP because you will have to add custom SAML claims or identification for approved devices.
Benefits of integrating with Azure AD:
a) Leverage on existing federation with O365.
b) Protect the resources with Azure AD conditional access.
c) Control on which devices can access the resource using Intune and Azure AD conditional access.
d) Force “Approved Clients” for the browser applications. Allow Qualys to be opened up only with “Intune managed Browser” and apply Intune App Protection Policies for managed browser to prevent data leakage.
c) All of the above at no additional cost as you have already invested in your O365 infra setup.
Actual steps:
a) Logon to your Azure AD portal with Global Administrator rights.
b) Follow the article provided below to configure the app that is not in the Azure AD app gallery.
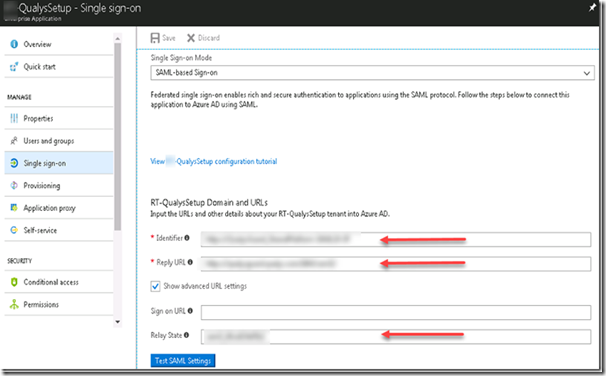
c) You will need two URLs i) Identifier and ii) Reply URL. Relay URL is not mandatory.
d) Create the metadata file and share it with Qualys. Activate the Certificate.
The steps are very well documented at the link below.
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-saas-custom-apps
Follow the steps above and create an application in Azure AD. Name it in such a way that users can easily identify it.
You will need Identifier and Reply URL from Qualys. Configuring Relay URL is not mandatory though that’s the location users will be redirected to once logged on.
Identify the username attribute to be sent in SAML token and share the metadata XML with Qualys. Dont forget to activate the cert.
End user Experience:
a) User Logs on to https://myapps.microsoft.com . Authenticates with normal process as he/she would do for https://portal.office.com.
b) Once logged on user will find the app displayed as “QualysApp” or whatever you named it.
c) User clicks on the link and SSOs to the Qualys dashboard.
Just imagine the possibilities that this throws at you. There is a “Provisioning” tab you see. That “Provisioning” helps you to create accounts on Qualys using Azure AD.
What this translates to is an integrated IAM functionality. If you dont use “provisioning” you will have to manually or find a way to sync your accounts with Qualys. I have not yet done this and am reaching out to Qualys for further help on this integration however, with this we would have achieved a zero touch provisioning of Qualys cloud service.
The end user is happy and so is the Azure AD Administrator who can now proudly go back to his security team and bosses showcasing the power of Azure AD SAML integration.
Bonus point:
This site also falls under Azure AD “Conditional Access”. This enables you to dictate that only devices managed by Intune can access the site and that too only via approved clients (Intune Managed Browser) in this case. With some more fun playing around at “Intune App protection Policies” you can ensure that Vulnerability reports downloaded via this browser can only be stored in OneDrive for Business. Data does not leave your control pane.
Please leave a feedback and do share your views on the above blog post. This is my first ever blog on a public forum. I have written tons of technical documents; white papers and architecture documents for the companies I have worked for. However, this is the first time I am interacting publicly.
Your feedback is precious for me.